Phishing Site Takedown
Minimize customer exposure and brand risk by detecting and removing phishing sites worldwide with speed, evidence, and automation.
Remove Phishing Sites Before They Harm Your Customers
Every minute a phishing site stays online increases the risk of stolen credentials, fraudulent transactions, and brand damage. Many registrars and hosts are slow to act — or fail to act at all.
Unphish Phishing Site Takedown gives you the speed, evidence, and automation you need to remove phishing websites worldwide.
Why Phishing Site Takedown Is Critical
Phishing sites trick customers, damage trust, and exploit inconsistent platform responses.
Customer Safety
Phishing sites steal login credentials, payment data, and personal information.
Brand Trust
Victims often blame your brand, not the criminals behind the phishing site.
Speed Is Critical
The longer phishing sites stay online, the more customers are affected.
Platform Gaps
Registrars, hosts, and DNS providers respond inconsistently without proper escalation.
How Our Phishing Detection and Takedown Works
Continuous Detection
Our system monitors domains, threat feeds, SSL logs, and phishing databases for fraudulent sites impersonating your brand.
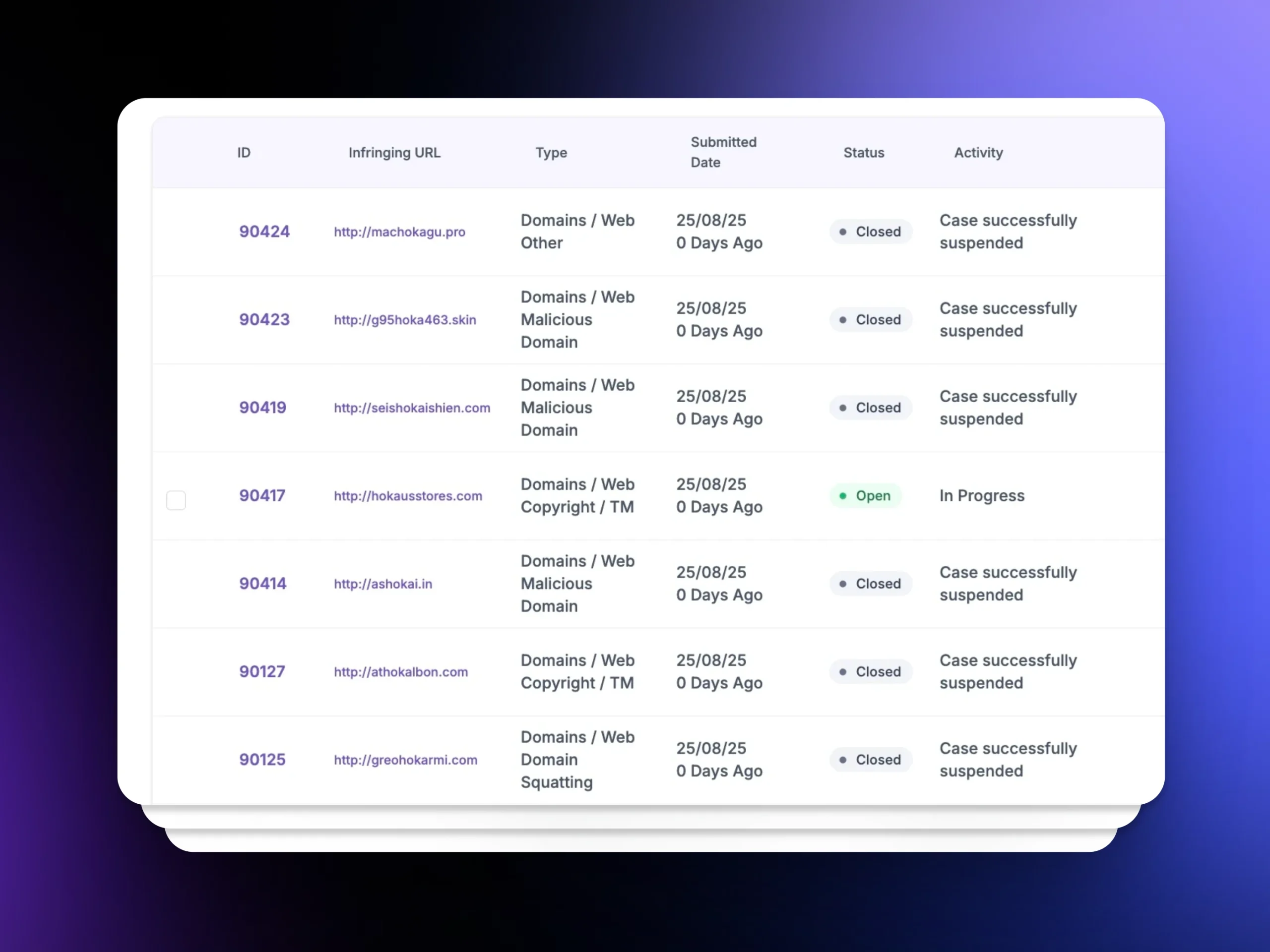
Evidence Collection
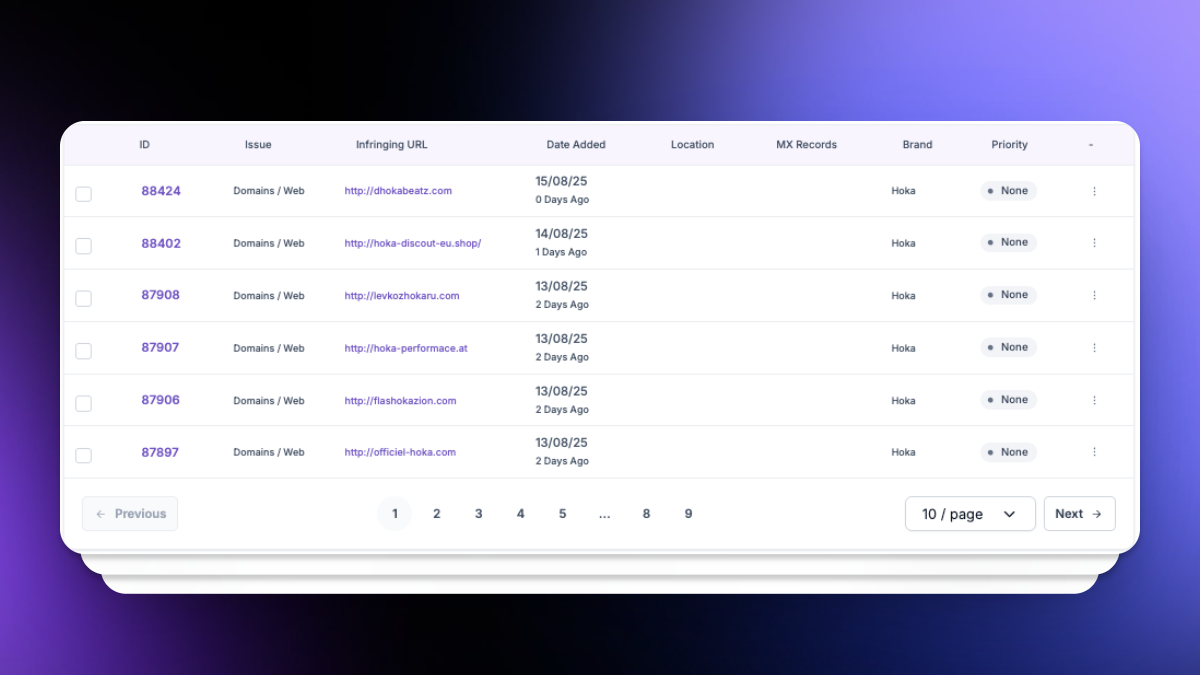
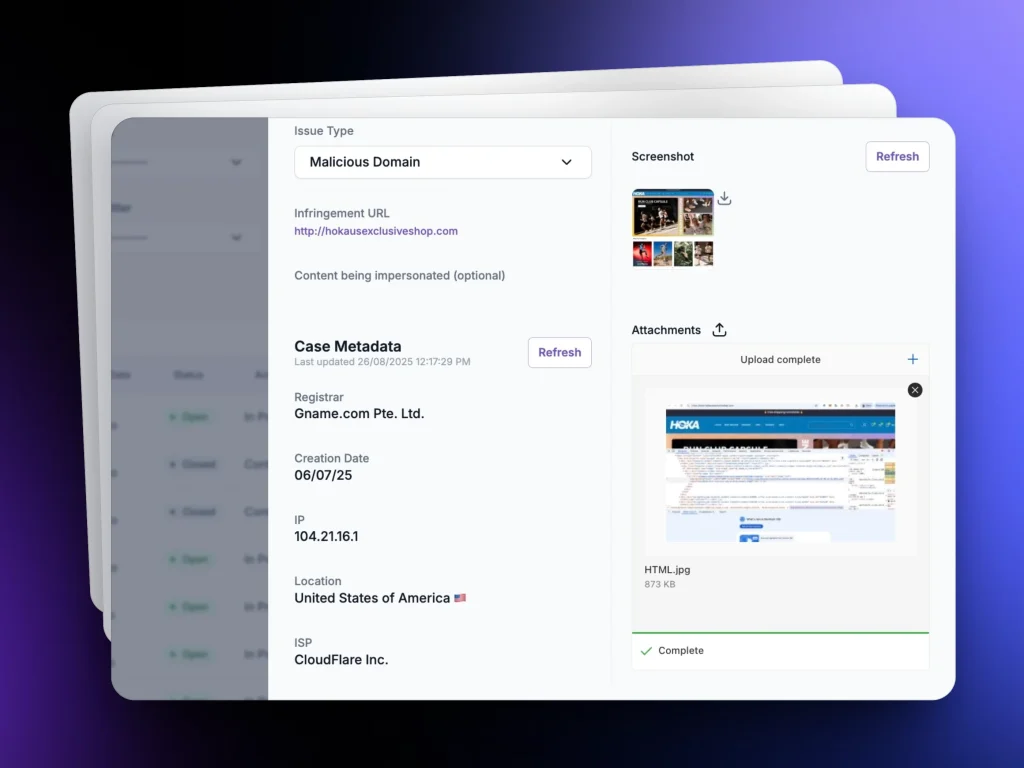
Each phishing site is captured with screenshots, WHOIS data, DNS records, SSL certificates, and timestamps — creating a ready-to-submit case file.
Automated Enforcement
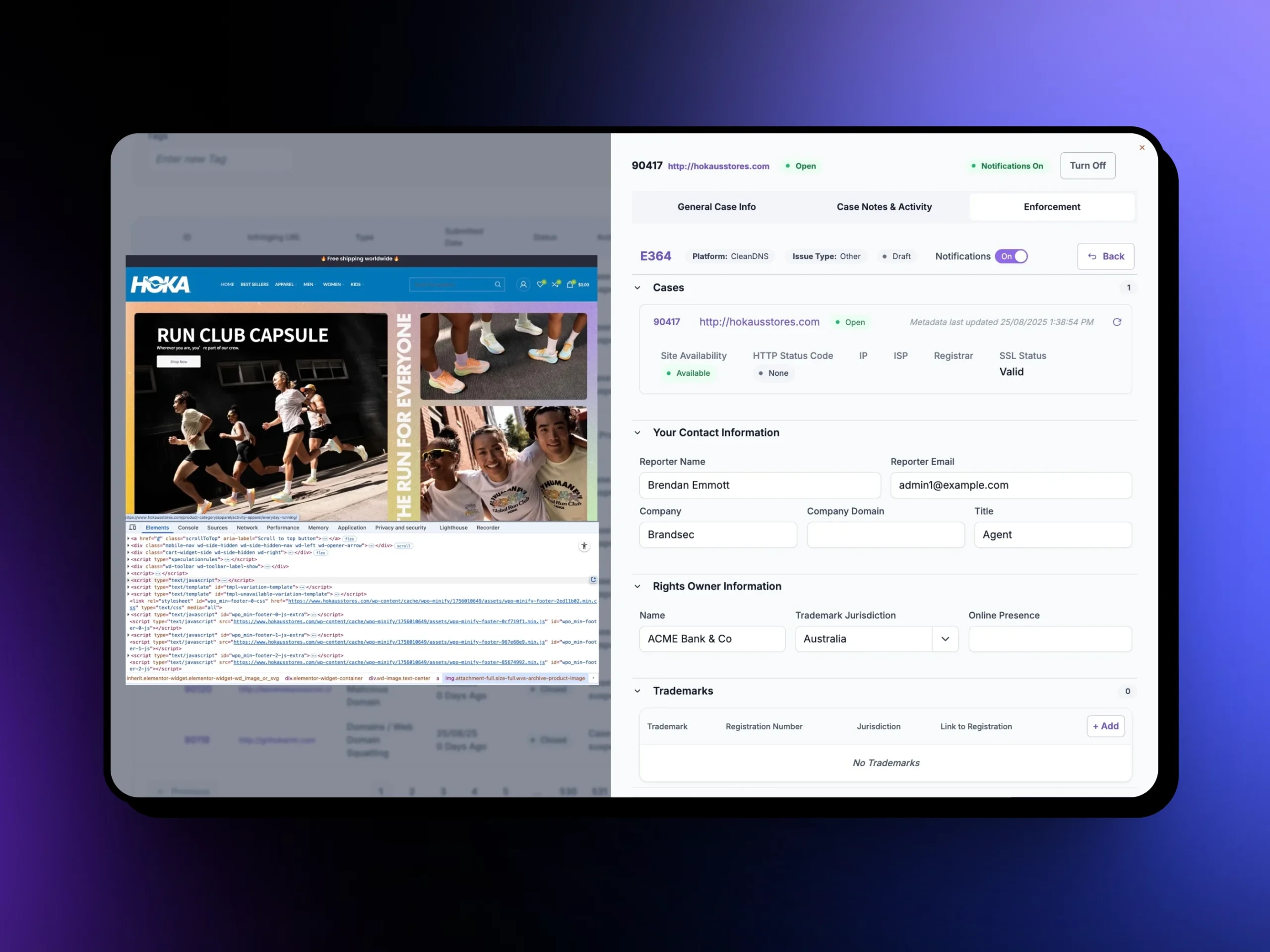
Unphish pre-fills registrar, host, and platform takedown forms with evidence and references to Abuse Policies or the ICANN RAA. For integrated platforms, API submissions are instant.
Escalation & Persistence
If providers ignore requests, Unphish escalates cases to registries, ISPs, or higher authorities (ICANN, CERTs), keeping pressure on until the site is down.
Features That Make Takedowns Fast & Reliable
Global Phishing Monitoring
Continuous detection across domains and threat feeds.
Evidence-Rich Case Files
Screenshots, WHOIS, DNS/SSL data, and timestamps.
Automated Takedown Submission
Fast removal through pre-filled forms or APIs.
Escalation to Authorities
Registries, ISPs, ICANN, or CERT escalation when needed.
Re-Activation Monitoring
Track and remove reappearing phishing sites.
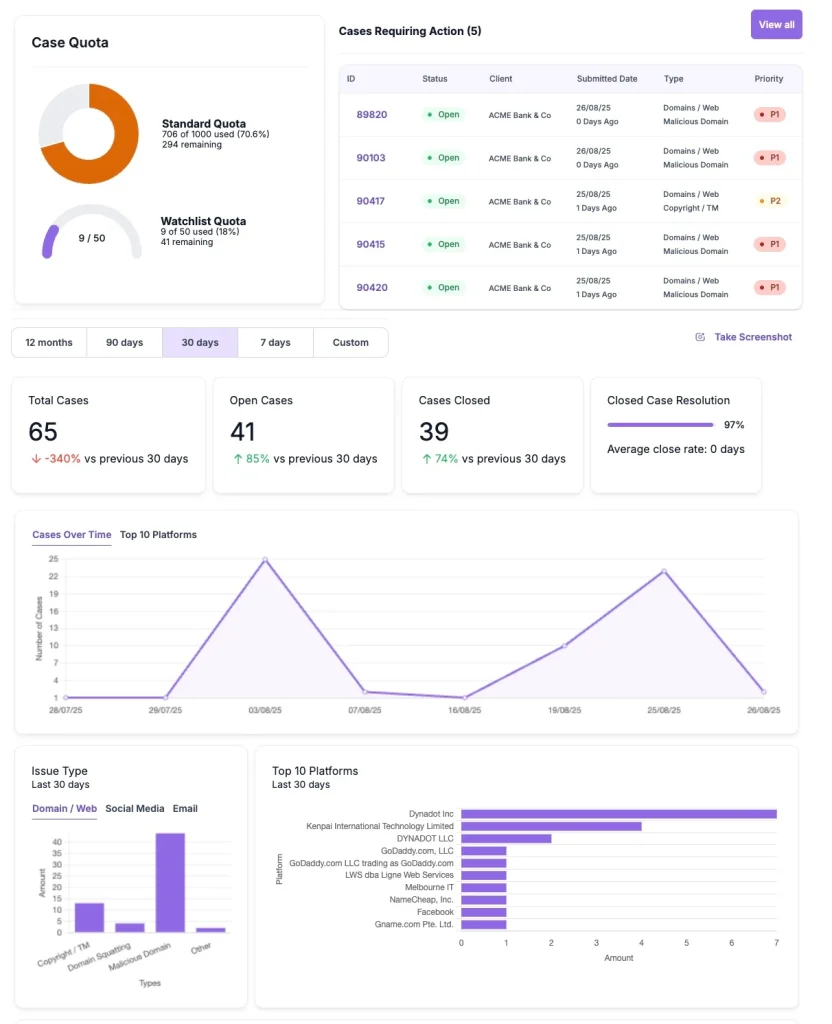
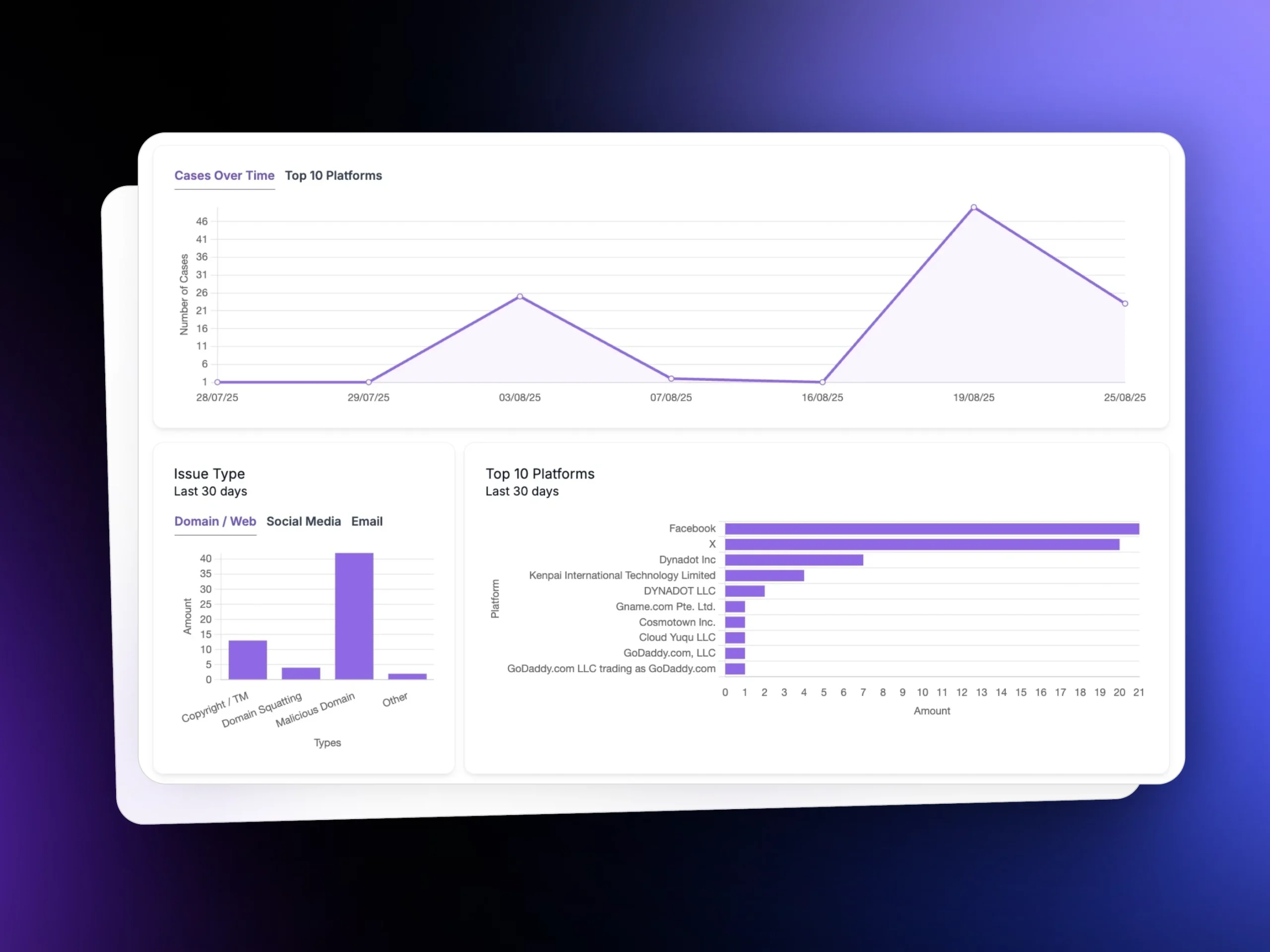
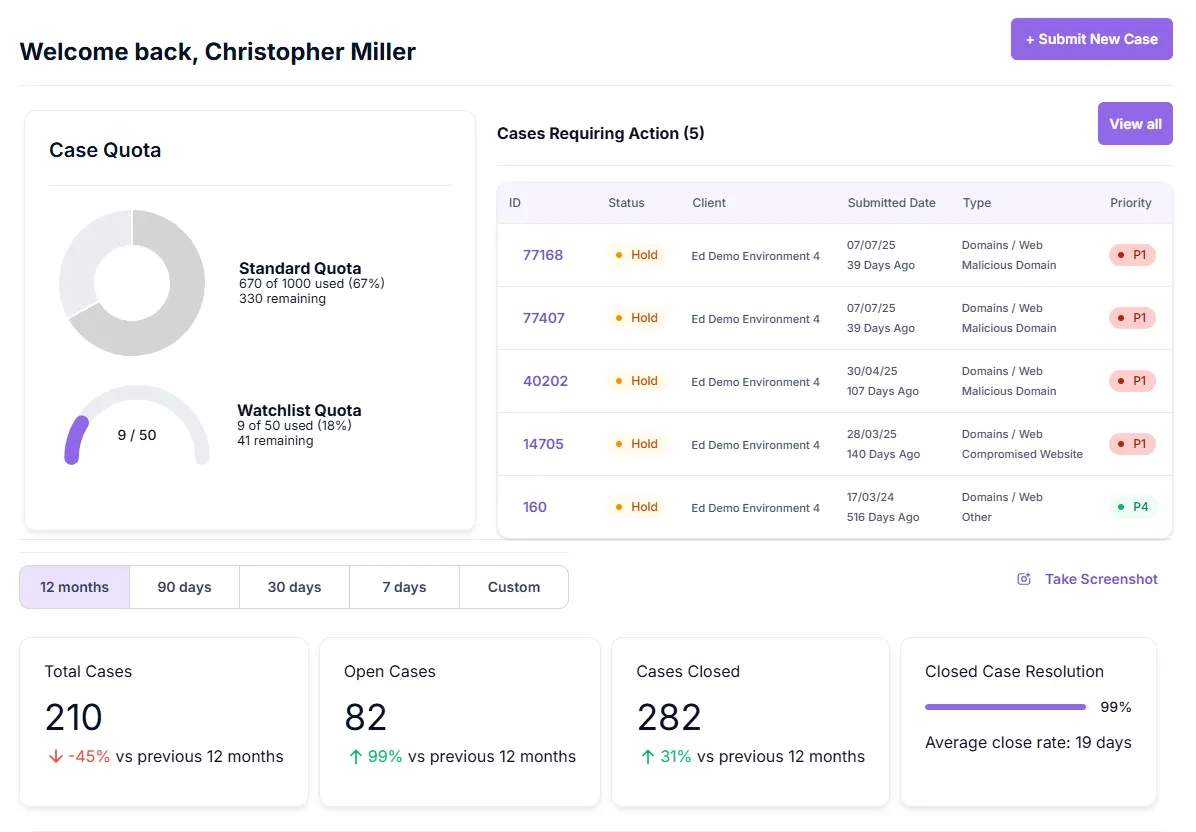
Analytics & Compliance Reporting
Dashboard with takedown metrics and audit-ready reports.
Why Choose Us for Brand Protection
We combine speed, automation, and policy-aligned enforcement for reliable phishing removal.
Speed & Automation
Faster detection-to-removal than manual reporting.
Policy-Aligned Complaints
Takedown requests platform rules for higher success.
Escalation Expertise
Expert guidance when providers fail to act.
Proof & Accountability
Every takedown logged, tracked, and verified.
How Unphish Compares
See the advantages of Unphish over manual reporting or monitor-only tools.
| Unphish | Manual Reporting | Basic Monitoring Tools | |
| Detection | Global, automated | Manual search | Alerts only |
| Evidence Collection | Full (WHOIS, DNS, SSL, screenshots) | Ad-hoc | Partial |
| Enforcement | Automated + escalation | Slow | Rare/limited |
| Verification | Yes | No | No |
| Reporting | Real-time dashboards, exports | Manual | Basic |


Typical Outcomes from Phishing Site Takedown
Minimize risk and protect customers with rapid, evidence-backed takedowns.
Phishing Site Takedown FAQs
Answers to the most common questions about phishing site takedown.
1. How fast can phishing sites be taken down?
2. How does Unphish detect phishing sites?
3. What evidence is included in takedown requests?
1. What evidence is submitted with takedown requests?
2. What happens if the same attacker sets up new phishing sites?
3. What happens if a registrar, host, or platform ignores a complaint?
Don’t Let Phishing Sites Harm Your Customers
Protect your brand and customers with fast, reliable phishing site takedowns.