Test Security
Unphish detects leaked questions, disrupts cheating services, and removes counterfeit credentials—preserving exam integrity across social, messaging, web, and marketplace
Stop Leaks and Cheating Before They Undermine Trust
High-stakes exams—from medical and professional qualifications to financial certifications—are prime targets for fraud. Criminal groups leak exam content, sell fake answers, solicit candidates on social media, and distribute counterfeit certificates.
Unphish Test Security addresses the entire fraud supply chain: detecting leaks, removing illicit content, and shutting down solicitation networks before they compromise your exams.
Why Test Security Is Essential
Exam integrity, candidate trust, and institutional reputation depend on proactive protection.
Integrity at Risk
Leaked content devalues exams and undermines qualification credibility globally.
Active Solicitation
Fraud networks solicit candidates daily across social and messaging platforms.
Reputation on the Line
Reputational damage escalates when employers and regulators lose confidence.
Real Financial Impact
Revenue suffers as counterfeit services and investigations drain resources.
How Unphish Protects Exams
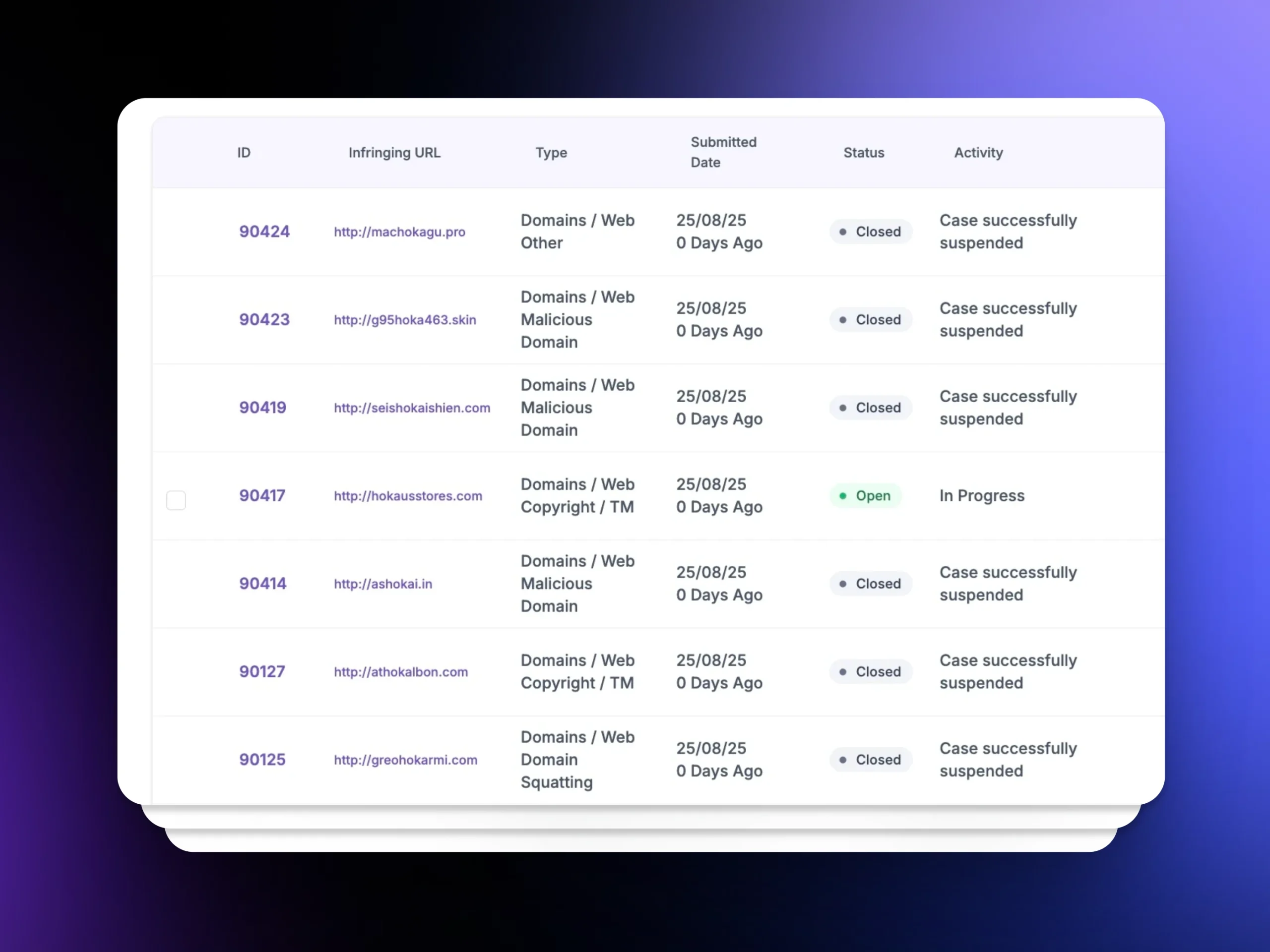
Detecting Leaked Test Material
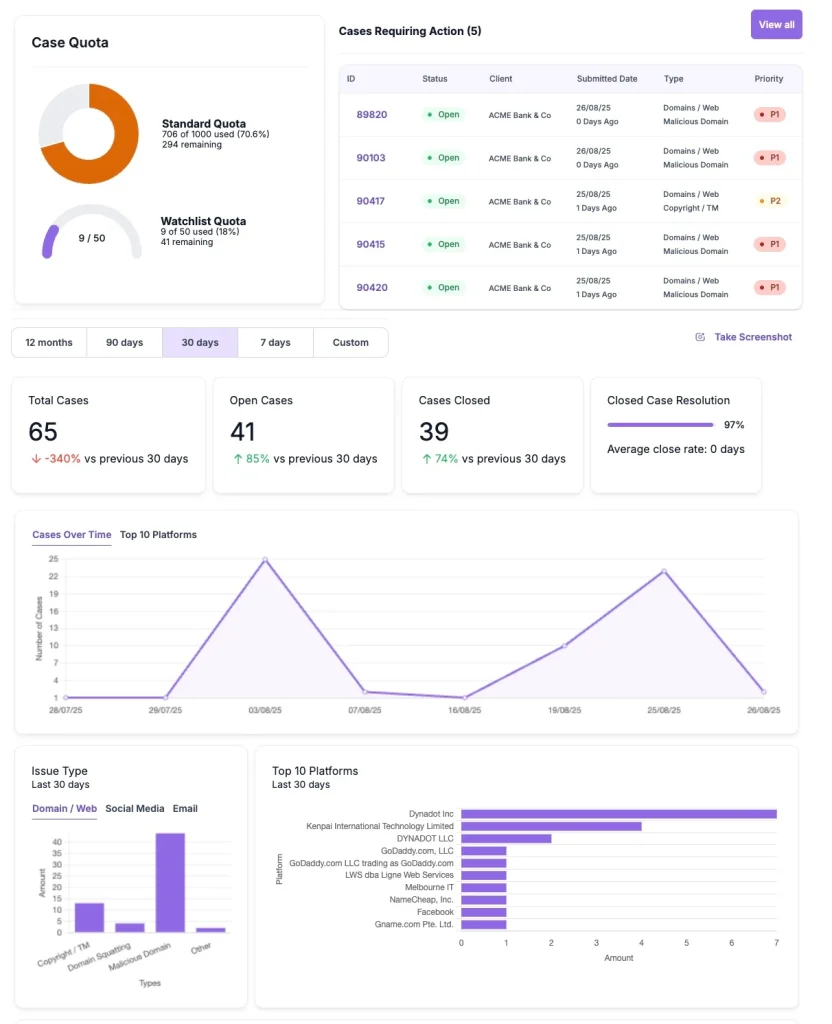
We continuously scan the open web, social media, forums, marketplaces, and messaging apps to identify leaked questions, answer keys, and prep content that violate exam confidentiality. Signals are prioritized for sensitivity, recency, and reach to enable rapid response.
Stopping Solicitation & Cheating Services
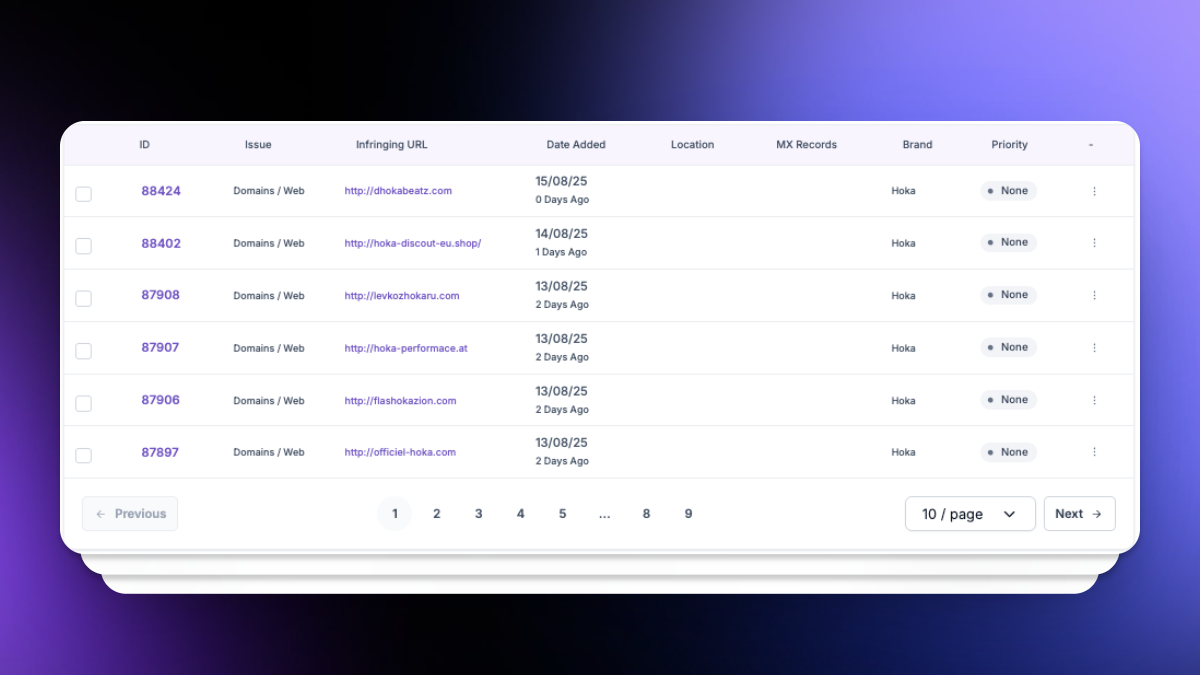
We monitor for “guaranteed pass” offers, cheating devices or software, test-taking impersonators, and paid access to test banks. Listings, posts, and landing pages are collected and mapped to the networks coordinating them.
Enforcement & Removal
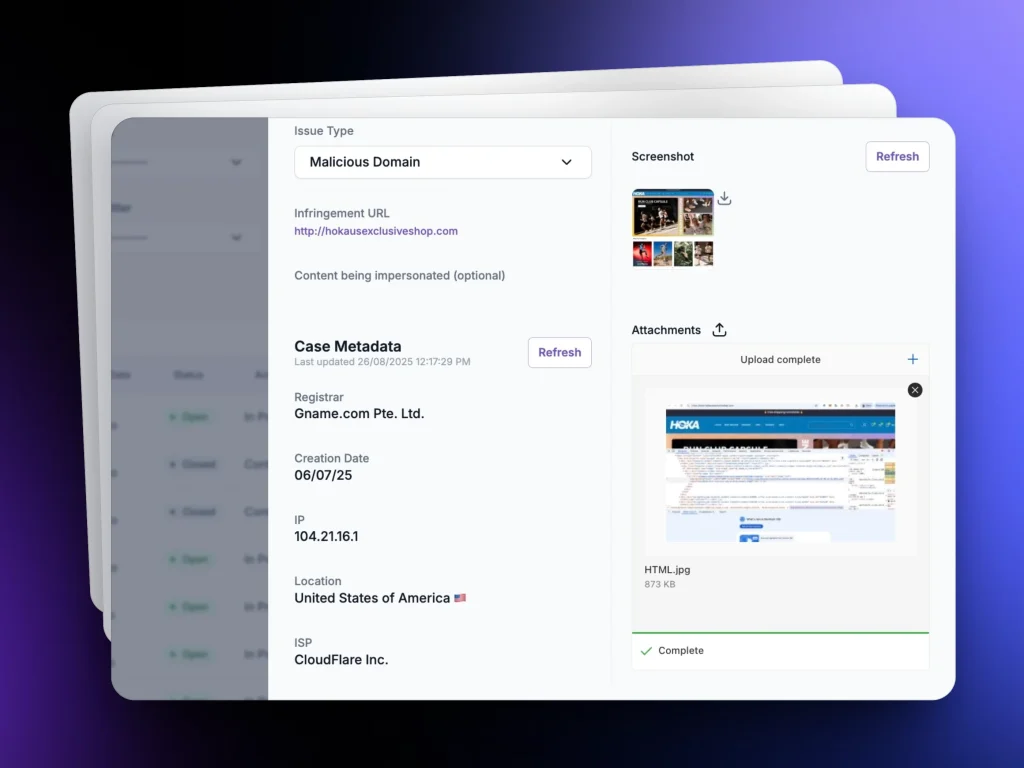
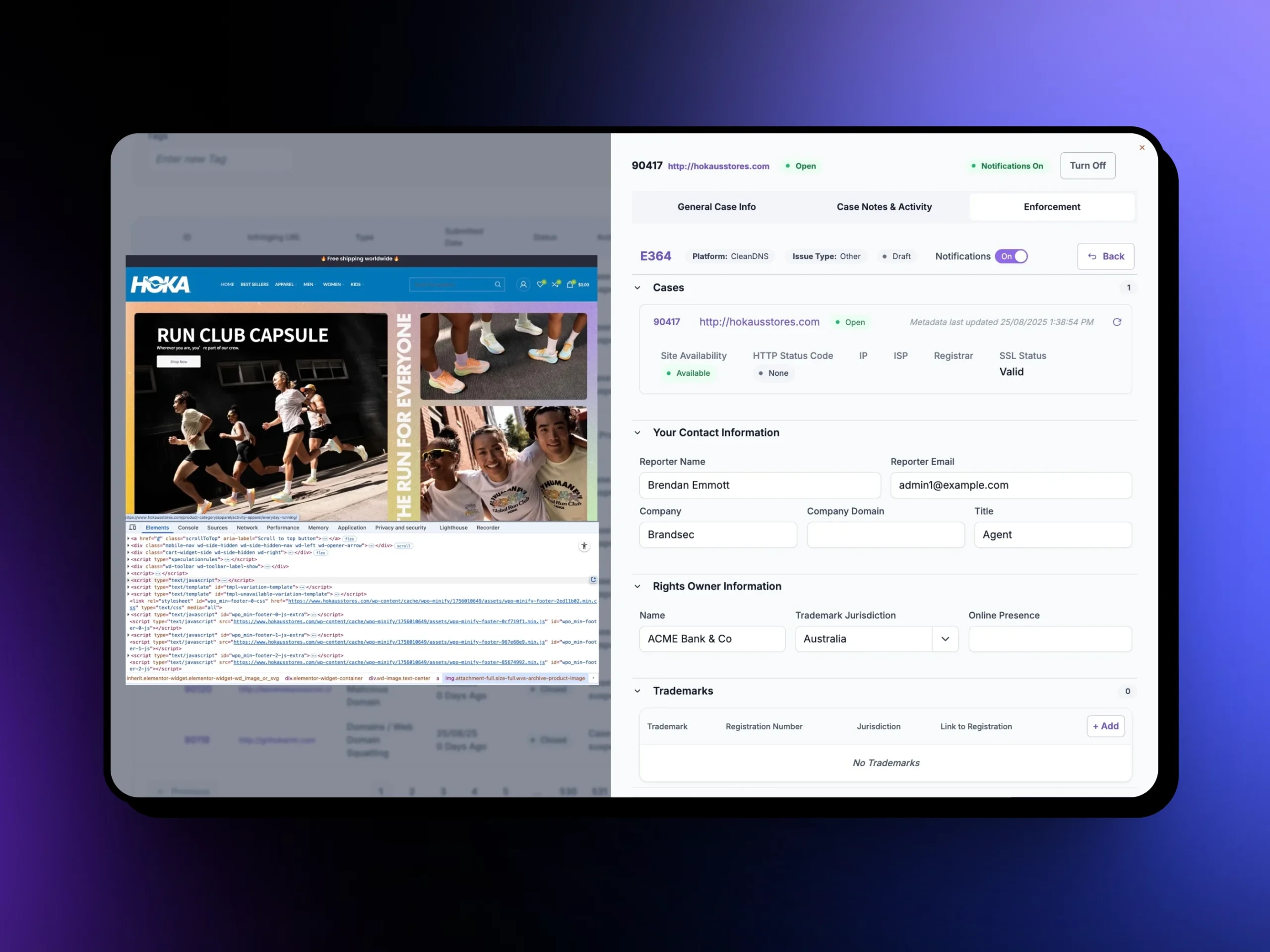
Using policy-aligned complaints and pre-formatted templates, Unphish submits takedowns to platforms, registrars, and hosts. Where needed, we escalate to regulators and enforcement bodies to ensure swift removal and deterrence.
Counterfeit Document Tracking
We detect and remove fraudulent certificates and forged attainment records sold online, helping prevent unqualified individuals from entering regulated professions and protecting public trust.
Features That Power Test Security
Leak Detection
Find leaked questions, answers, and prep content early.
Service Disruption
Remove “pass guarantee” offers and cheating solicitations.
Social & Messaging Monitoring
Track Telegram, WhatsApp, forums, and emerging networks.
Certificate Enforcement
Detect and remove fake certificates and forged results.
Automated & Escalated Takedowns
Submit policy-aligned complaints and escalate when required.
Real-Time Dashboards
View threats, takedowns, and metrics in one place.
Why Exam Boards Choose Unphish
A complete, evidence-first approach trusted by credentialing bodies worldwide.
End-to-End
Coverage
From leaks to fake records, we disrupt the full fraud chain.
Cross-Platform Reach
Enforcement across social, messaging, domains, and marketplaces.
Evidence-First
Screenshots, metadata, timestamps, and forensic detail for every case.
Proven Approach
Built for industries where integrity and trust are non-negotiable.
How Unphish Compares
See the advantages of Unphish over manual reporting or monitor-only tools.
| Unphish Test Security | Manual Monitoring | Alerts-Only Tools | |
| Leak Detection | Proactive, multi-platform | Limited | Rare |
| Fraudulent Services | Identified & removed | Hard to track | Not covered |
| Counterfeit Certificates | Enforced | No | No |
| Enforcement | Automated + escalation | Manual | Alerts only |
| Verification & Reporting | Yes | No | Minimal |


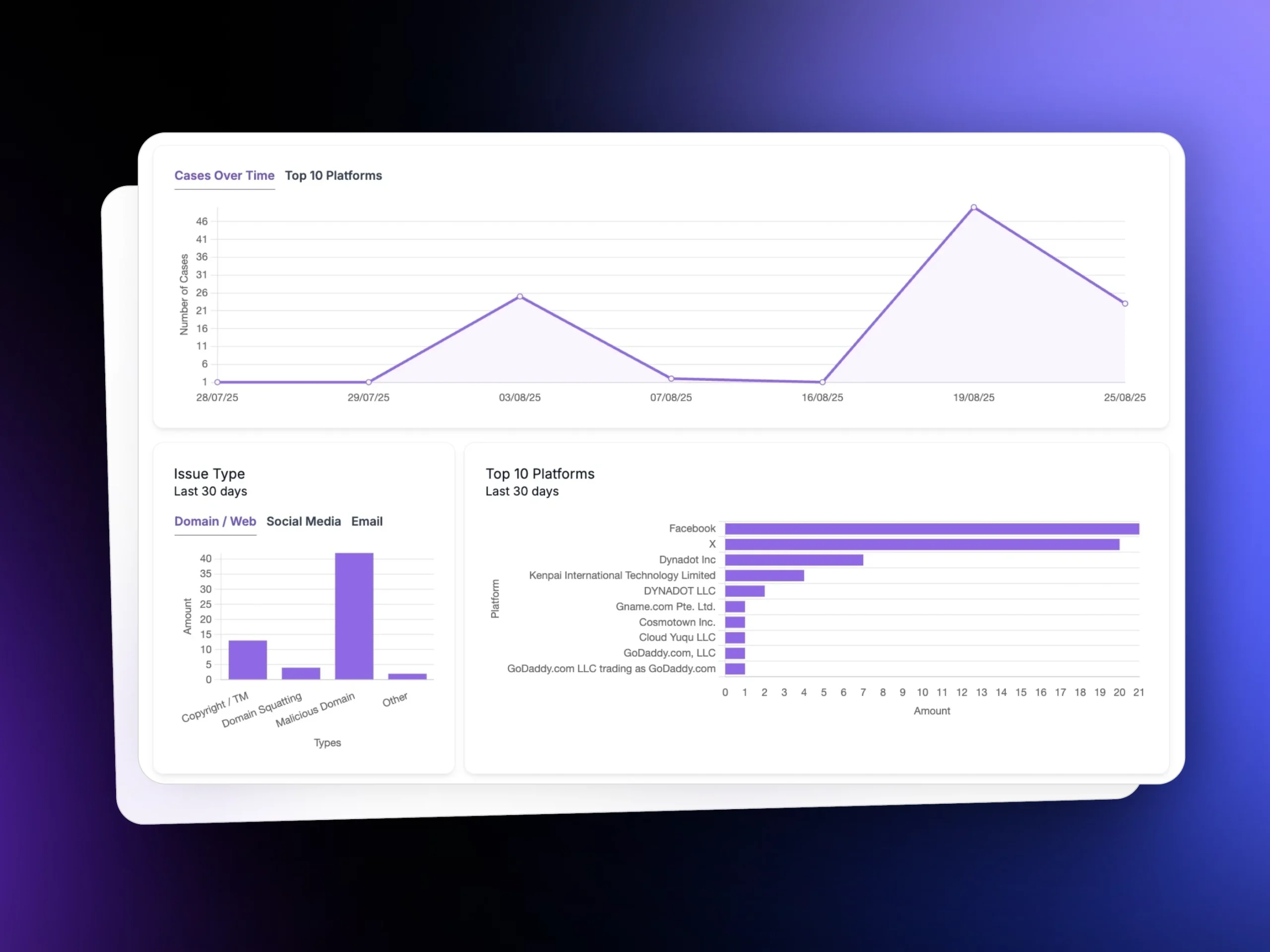
Measurable Protection for High-Stakes Assessments
Typical outcomes exam providers see after implementing Unphish.
Test Security FAQs
Clear guidance on how Unphish protects exam integrity, end-to-end.
1. What types of test fraud does Unphish address?
2. Which platforms are monitored?
3. How quickly is content removed?
4. Can Unphish detect leaks proactively?
1. What evidence is provided for each case?
2. How do you handle repeat offenders?
3. Can this integrate with exam provider workflows?
4. Do you support regulatory or audit reporting?
Safeguard the Integrity of Your Exams
Stop leaks, disrupt cheating services, and remove counterfeit credentials with Unphish.