Phishing Protection
Unphish protects your brand with fast, automated detection and takedowns, stopping phishing threats before they cause damage.
Phishing Protection That Works at the Speed of Attack
Unphish delivers AI-powered phishing detection and takedown, removing fake websites, domains, and impersonations before they damage your brand.
Why Phishing Protection Is Essential for Every Brand
Phishing attacks put trust, revenue, and reputation at risk. Unphish helps brands stay secure with proactive defense.
Customer Trust
Safeguard users from phishing emails, fake websites, and fraudulent apps, building long-term confidence in your brand.
Financial Security
Prevent costly fraud, account takeovers, and data theft that can directly impact your revenue and bottom line.
Reputation & Compliance
Defend your brand from impersonation, meet regulatory requirements, and protect years of hard-earned reputation.
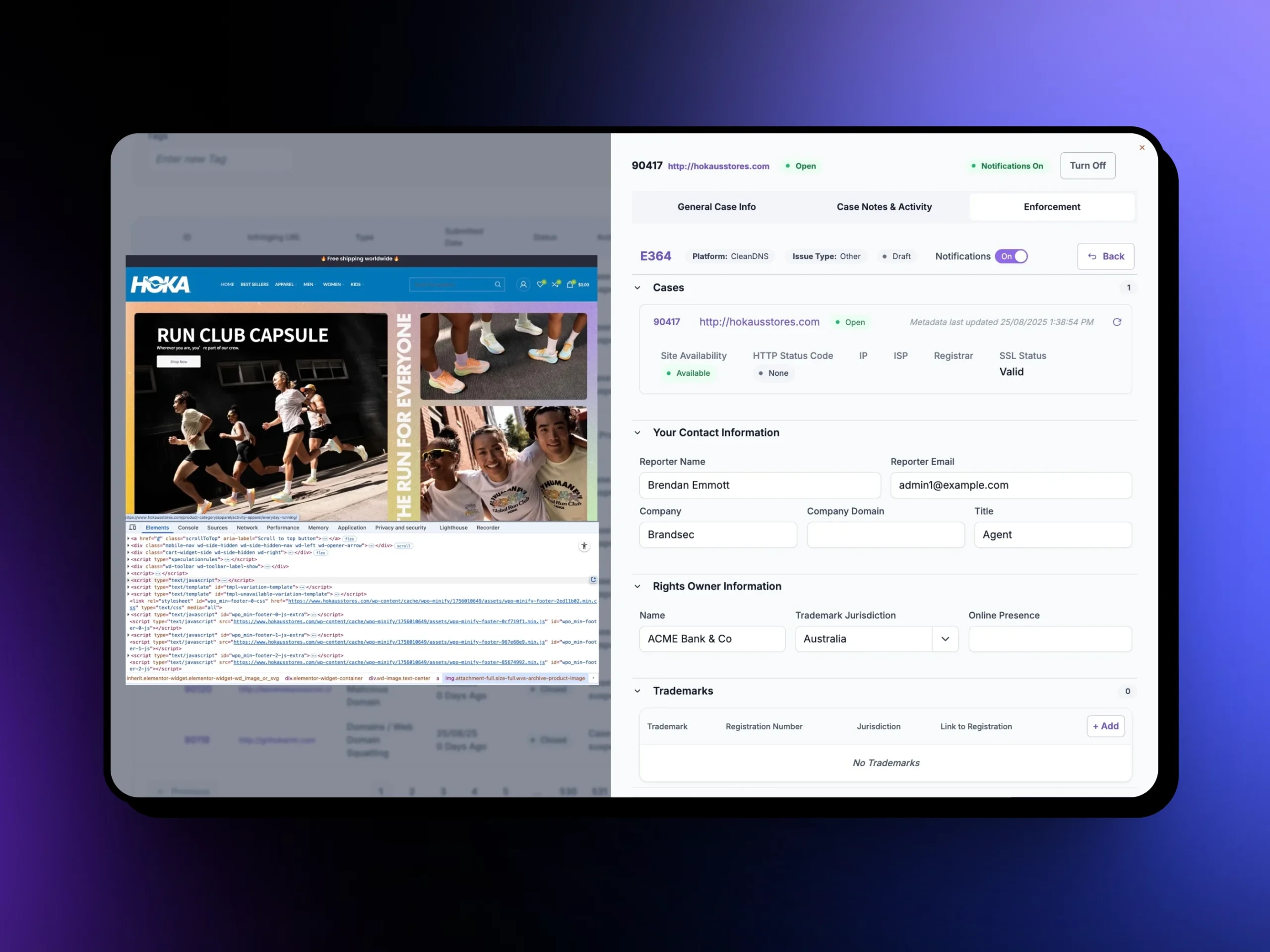
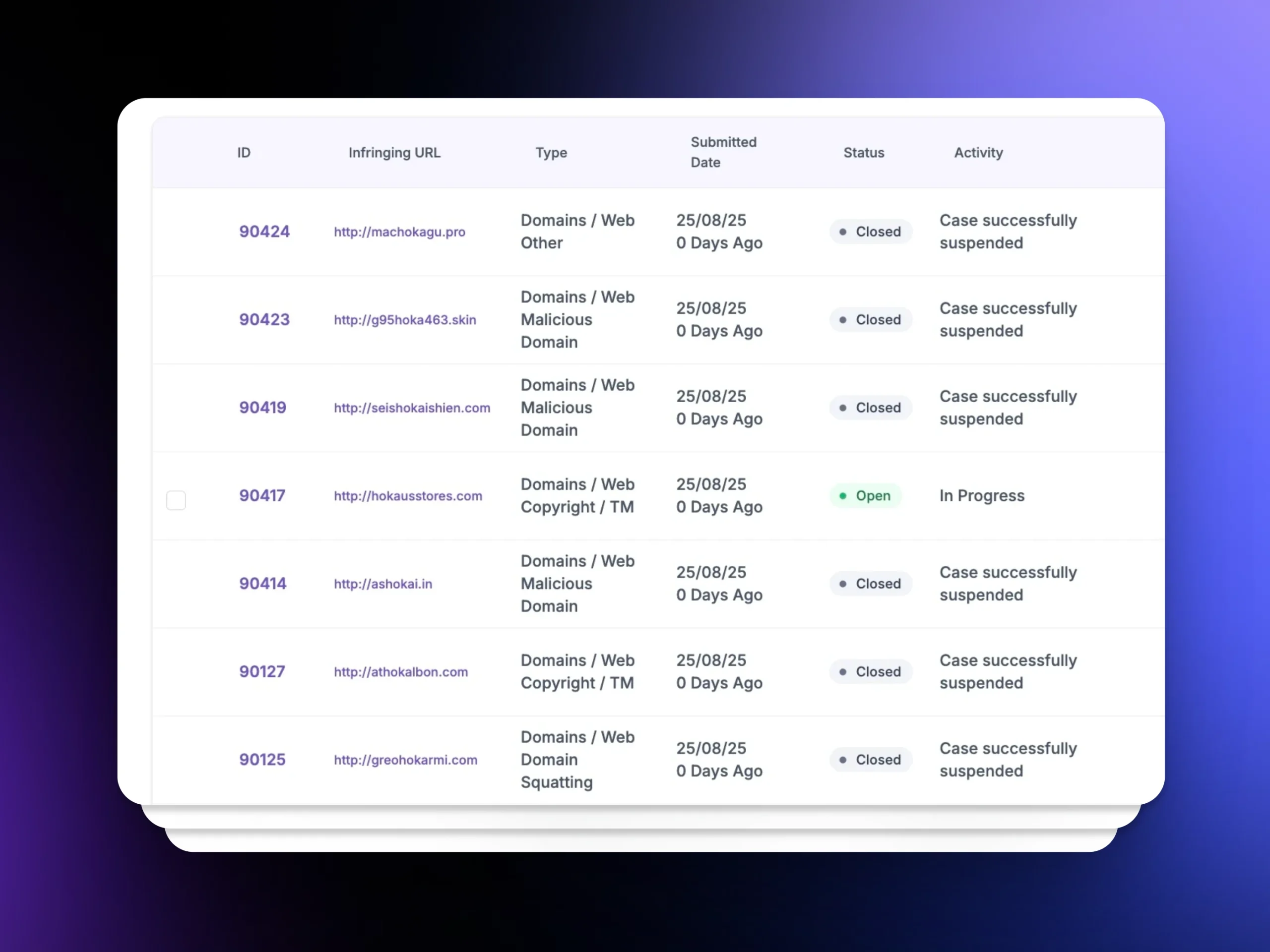
How Our Phishing Detection and Takedown Works
Key Features of Unphish’s Phishing Protection
AI-Powered Threat Detection
Identify phishing websites and fake domains at scale.
Automated Takedown Engine
Remove phishing sites faster with automation.
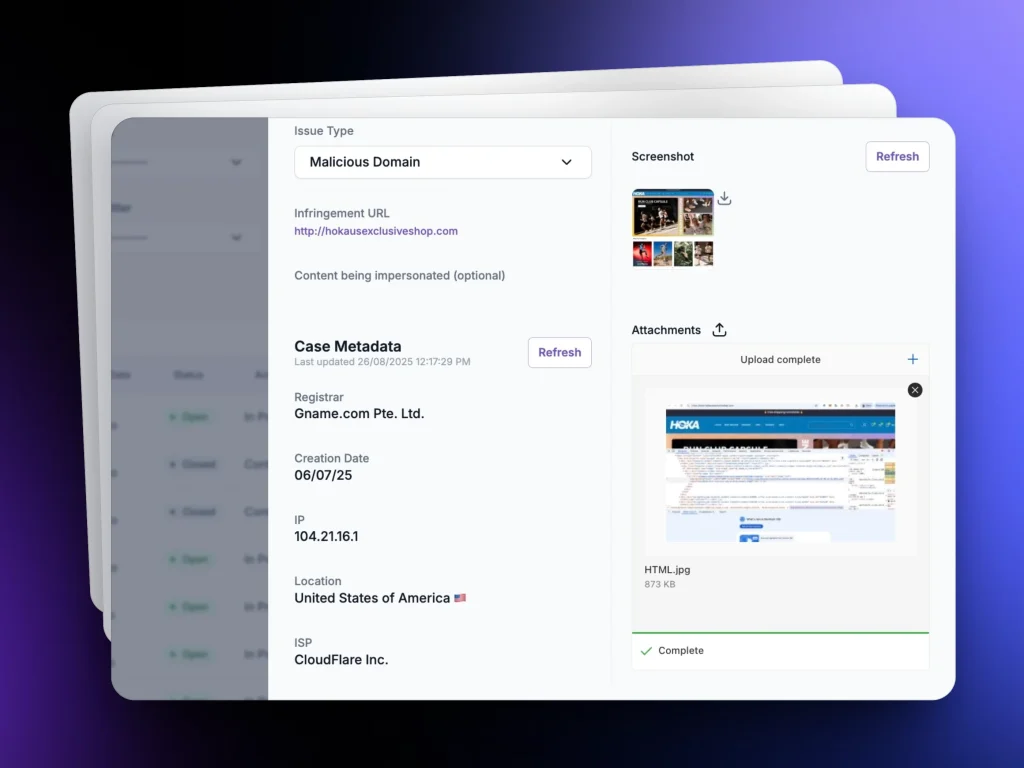
Evidence Collection Suite
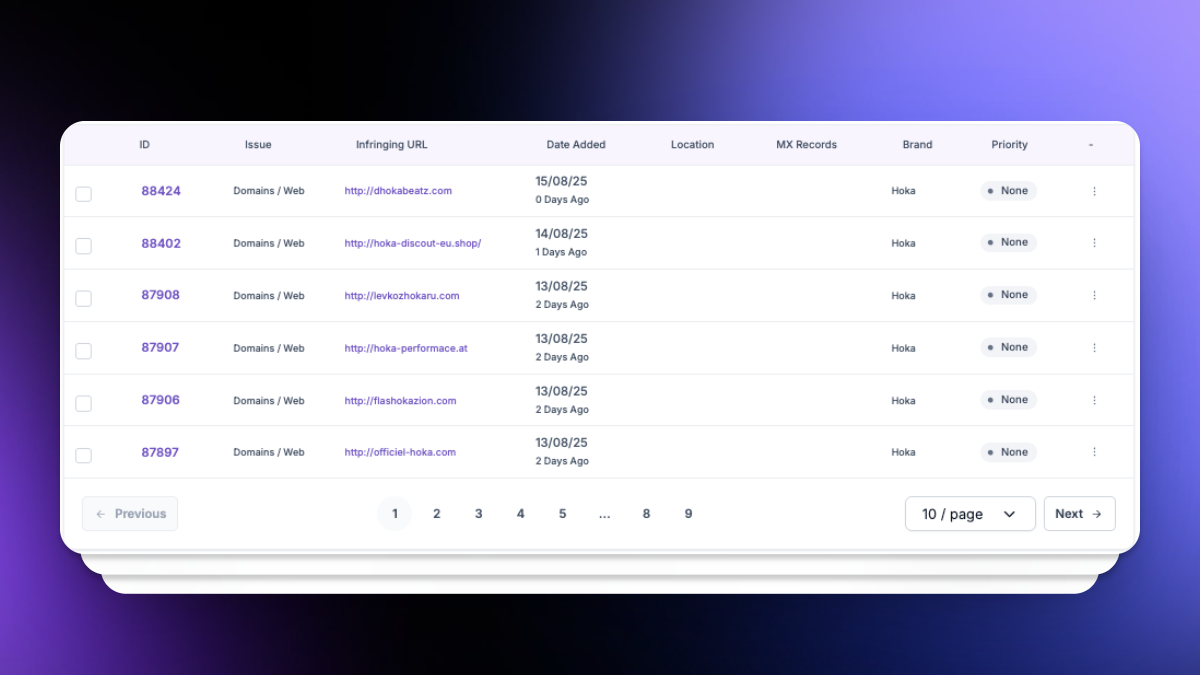
Screenshots, WHOIS, Meta Data, SSL & DNS data for enforcement.
Global Coverage
Phishing protection across domains, hosts, and social platforms.
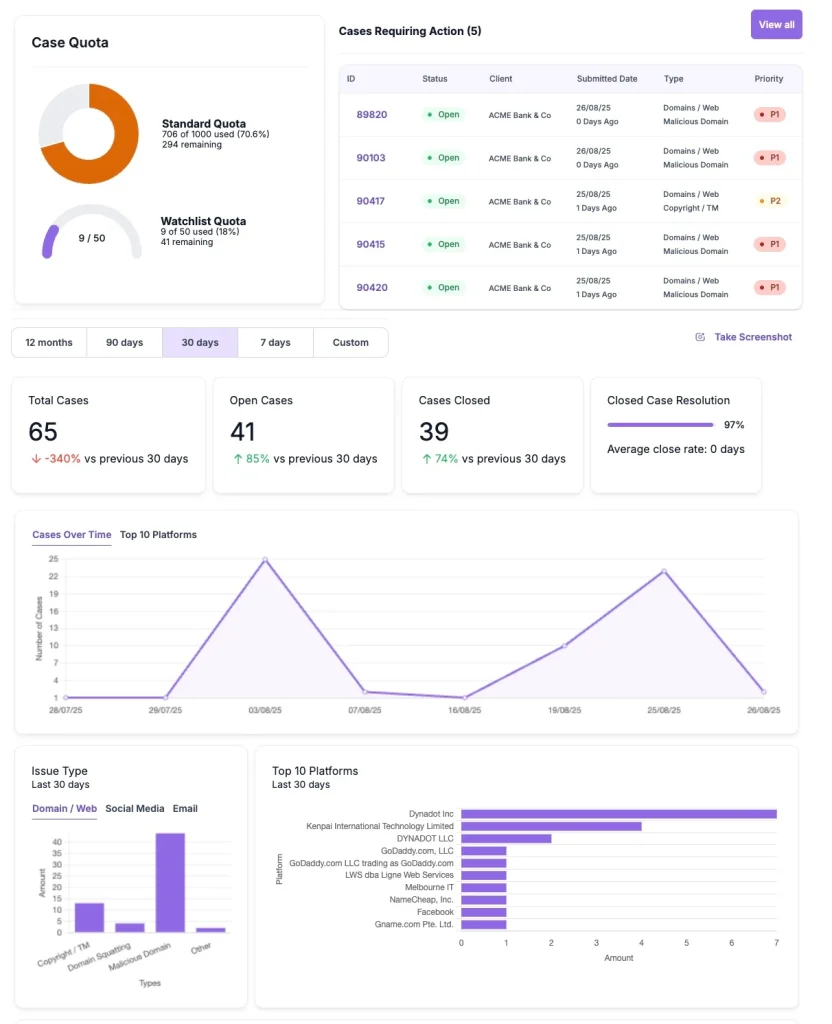
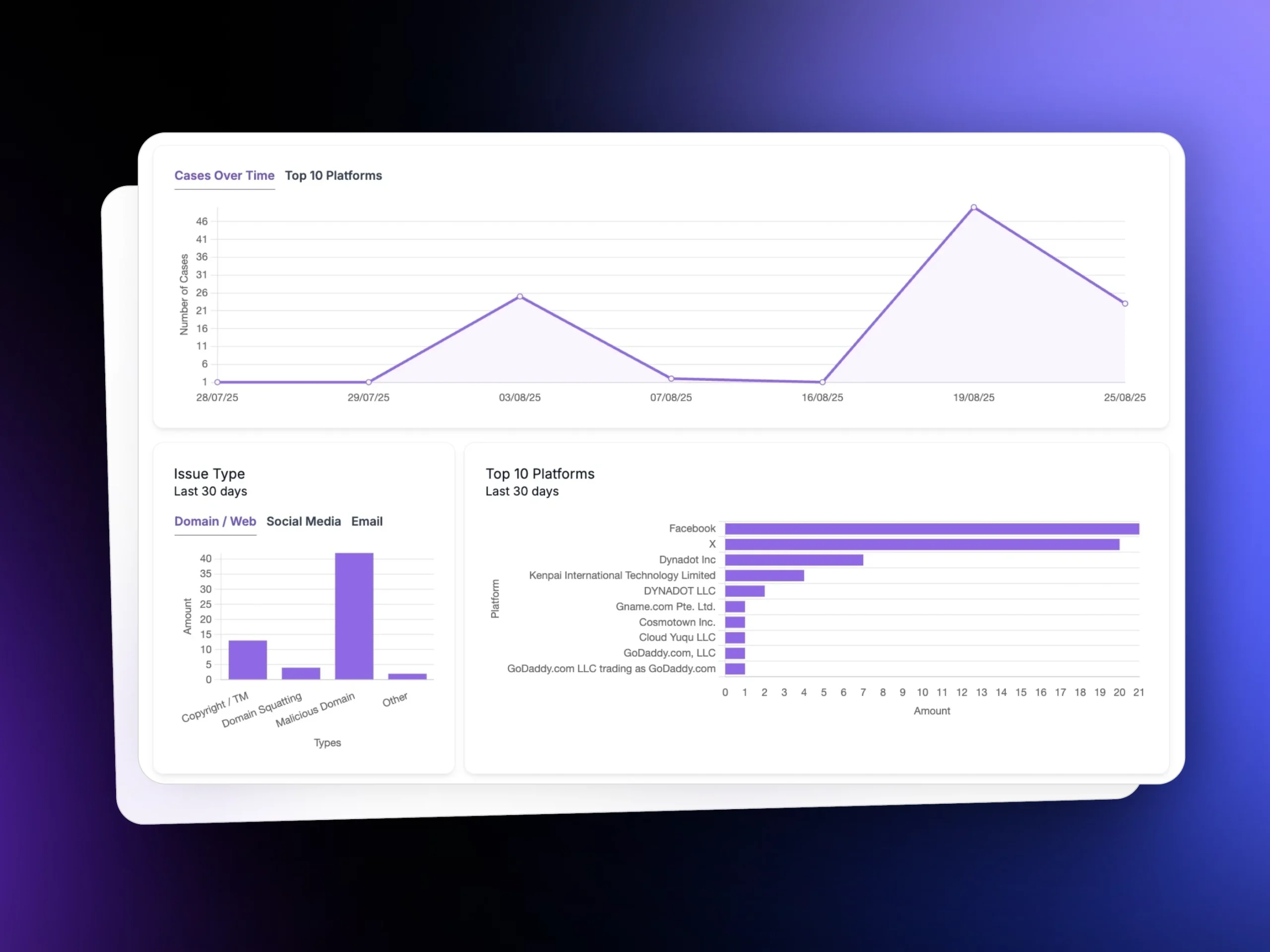
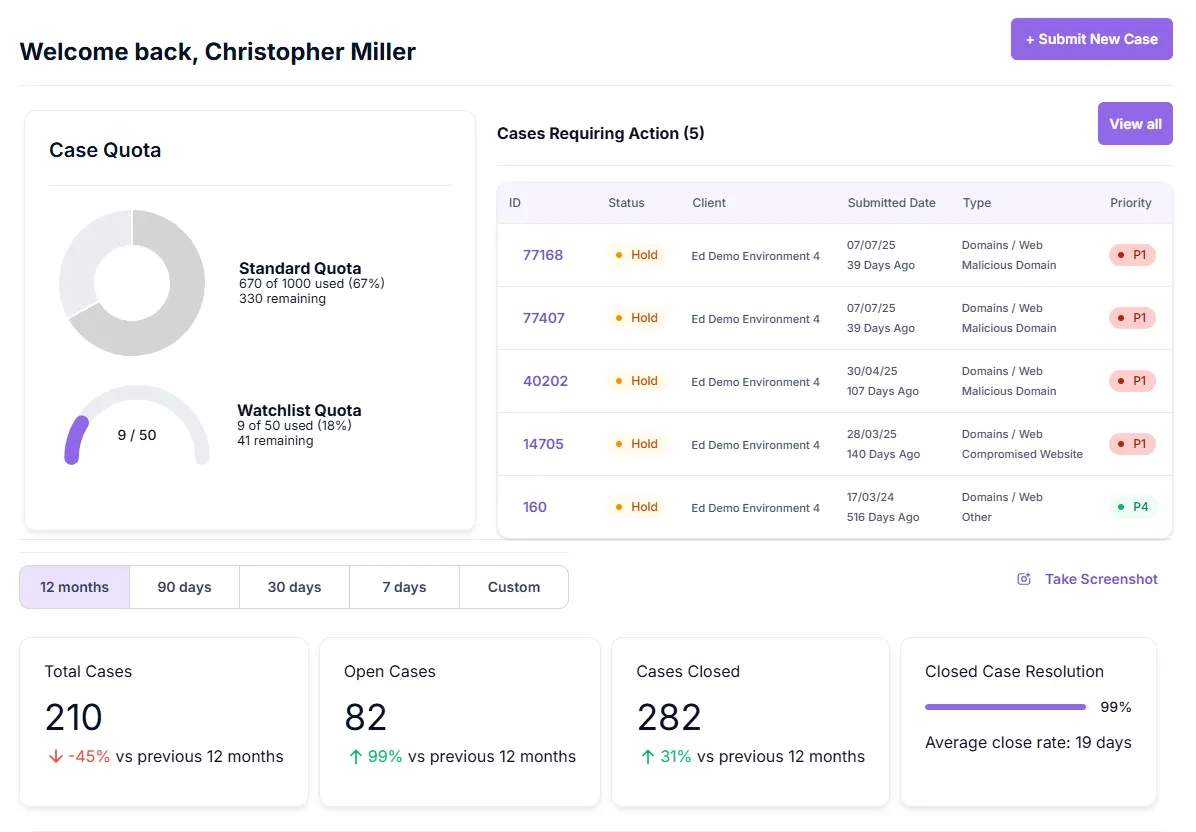
Real-Time Dashboards
Monitor phishing cases and takedown success.
Compliance-Ready Reports
Demonstrate phishing mitigation to regulators.
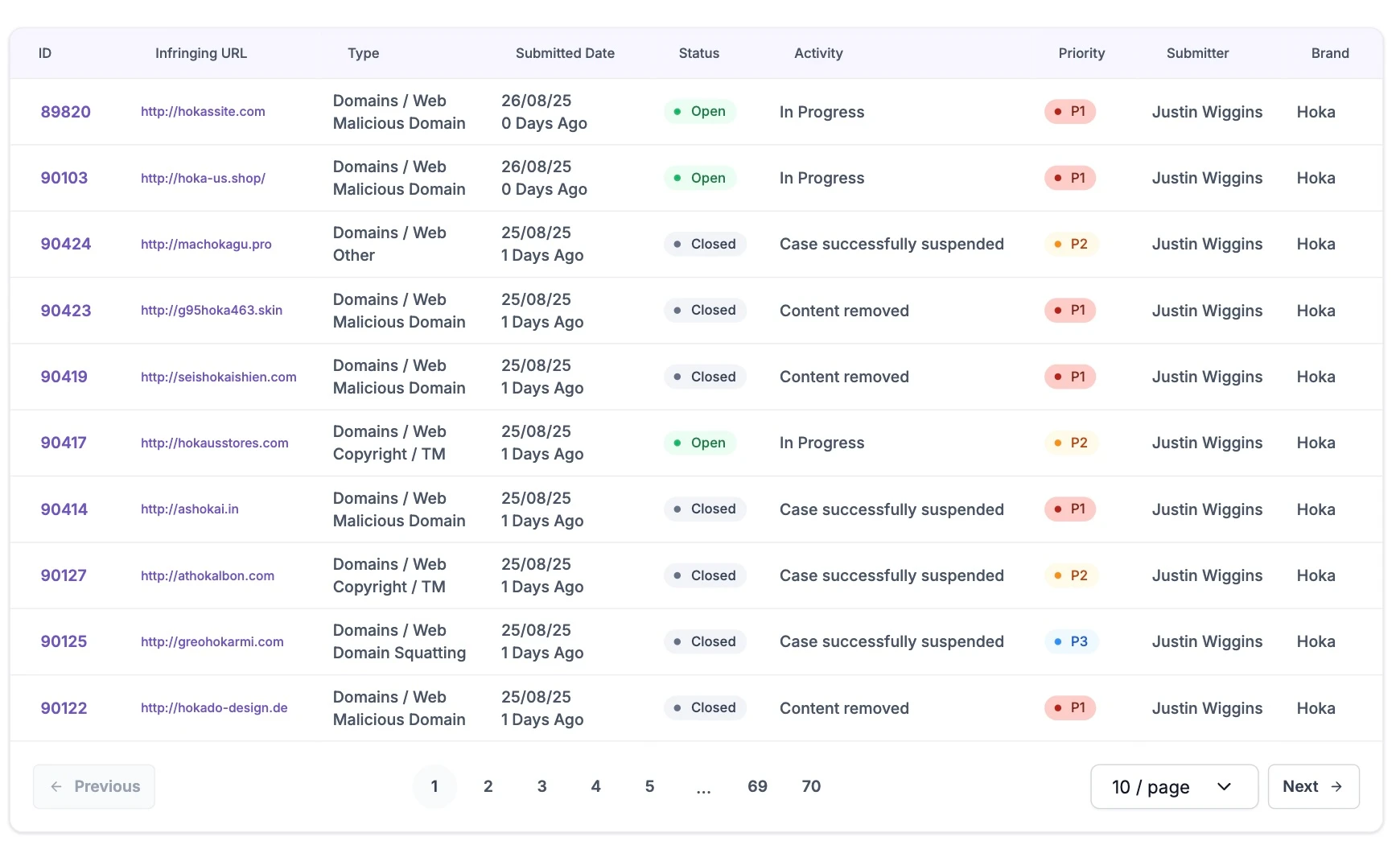
See Phishing Takedown in Action
Watch how Unphish identifies, removes, and reports phishing sites—showcasing real-time dashboards and takedown results.
Why Choose Unphish for Phishing Site Removal?
Unphish delivers faster, evidence-backed phishing site removal compared to traditional providers, protecting brands from fake websites and impersonation threats.
| Unphish | Self-managed | |
| Phishing Detection | AI engine scanning hundreds of data sources | Customer complaints, manual and google searches |
| Fake Website Takedown | AI-driven detection + instant action. Thousands of platforms takedown processes mapped and optimised | Manual takedown submissions are slow and resource-intensive, with each platform requiring different rules and processes. |
| Brand Impersonation Protection | Coverage across domains, social media, and marketplaces | Mostly reactive |
| Evidence Collection | Automated, Screenshots, Meta data, WHOIS, SSL, DNS for enforcement | Basic or no evidence |
| Compliance Reporting | Ready-to-share regulatory reports | None |
| Global Coverage | 24/7 monitoring across regions | Limited regional reach |


Unmatched Speed & Scale
Unphish protects brands at scale, detecting threats fast and acting even faster
Phishing Protection FAQs
Everything you need to know about how Unphish detects, mitigates, and tracks phishing threats.
1. How fast can phishing sites be taken down with Unphish?
2. What types of phishing attacks does Unphish protect against?
- Fake login and credential-harvesting sites
- Brand impersonation websites and social profiles
- Fraudulent mobile apps and marketplaces
- Phishing-as-a-Service (PhaaS) kits deployed at scale
- Executive impersonation scams and spear-phishing campaigns
- Lookalike domains using homoglyphs, typos, and subdomains
3. Does Unphish provide phishing protection on social media platforms?
4. What happens if a phishing site reappears after being taken down?
5. How does Unphish detect phishing sites?
- AI-driven detection for lookalike domains, fake pages, and suspicious activity
- Threat feed integrations for real-time intelligence
- Certificate Transparency (CT) log monitoring for new SSL certificates containing brand terms
- Visual analysis (logo and text recognition in screenshots)
- Passive DNS enrichment to uncover related phishing infrastructure
6. Is phishing protection global?
1. How is Unphish different from other phishing detection tools?
- Detection at scale (across web, social, and mobile).
- Automated evidence collection (screenshots, WHOIS, DNS, SSL).
- Automated enforcement (API-driven or form auto-population).
- Verification and reporting (so you know every takedown is successful).
2. Can Unphish integrate with my existing security systems?
3. How does Unphish prove compliance for regulators or auditors?
4. Do you only work with large enterprises, or can smaller businesses use Unphish?
5. How much does phishing protection cost?
6. Why is phishing protection critical for my brand’s reputation?
Stop Phishing Attacks Before They Spread
Protect your customers, your brand, and your reputation. Request a demo of Unphish today