Phishing Response. Rebuilt
for Speed and Scale.
Legacy takedown processes are slow and manual.
We reimagined the whole thing.
Core Features

AI-Powered
Takedown Engine

Same-Day Response
Custom Workflows

Client Notification
System

Case Categorisation
(Crypto, Phishing)

Analytics
Dashboard

Intelligent
Escalation Paths
API-Ready (Future
Roadmap)

AI-Powered
Takedown Engine

Same-Day Response

Custom Workflows

Client Notification
System

Case Categorisation
(Crypto, Phishing)

Analytics
Dashboard

Intelligent
Escalation Paths

API-Ready (Future
Roadmap)

AI-Powered
Takedown Engine

Same-Day Response

Custom Workflows

Client Notification
System

Case Categorisation
(Crypto, Phishing)

Analytics
Dashboard

Intelligent
Escalation Paths

API-Ready (Future
Roadmap)
How Unphish Works
Fake Websites, Domains, and Marketplaces

Domains & Subdomain Analysis
Monitors for brand names,look-alikes, and typo variants across global TLDs and subdomains.
Mobile App and Social Media Impersonation
Social Media Discovery
Scans platforms like Facebook, Instagram, Telegram, WhatsApp, and X for fake profiles.
Phishing Kits and Look-alike Pages

Visual Similarity & HTML Fingerprinting
Our system detects and compare suspicious pages to your real site using advanced matching technique.
URL Watchlist

Threat Feed Correlation
Monitors potentially threatening domains that target your brands. Analyses traffic and patterns from registrar/registry sinkholes to identify threat actor infrastructure.

Copyright Abuse and False Affiliation

Keyword Analysis
Flags phishing language, financial lures, login requests, crypto wallet prompts, and scam patterns—across
Mobile App and Social Media Impersonation

Social Media Discovery
Scans platforms like Facebook, Instagram, Telegram, WhatsApp, and X for fake profiles.
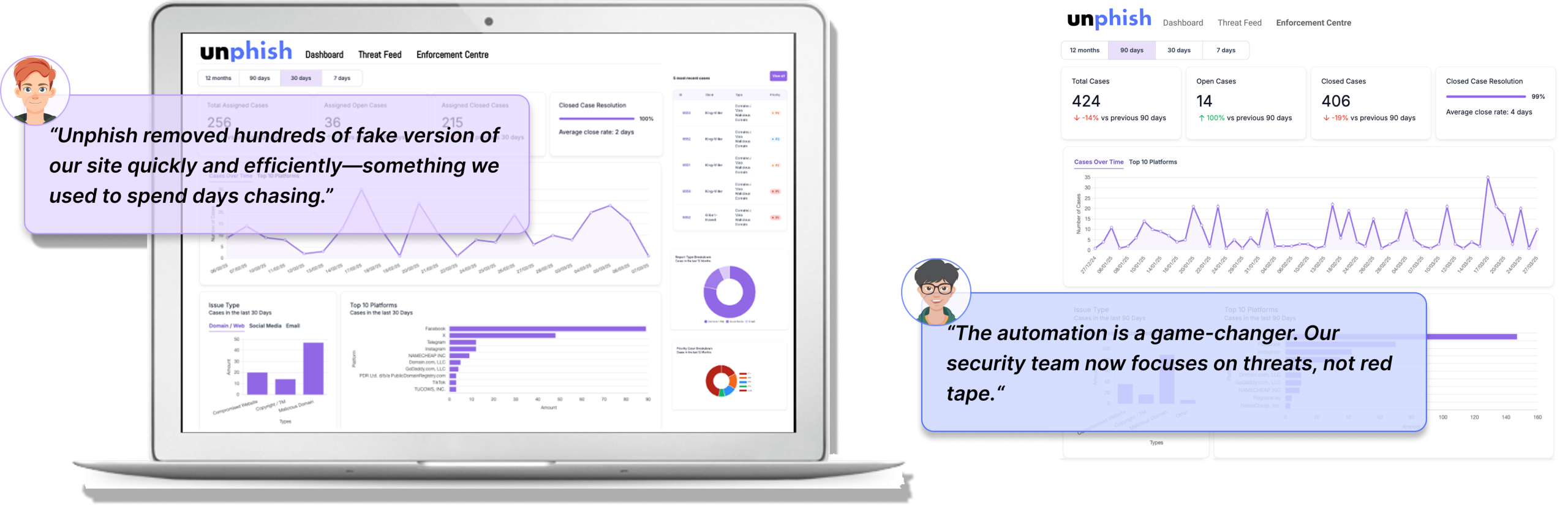
Client Feedback